What is it
Just Enough Administration (JEA) is an administrative technology that allows you to apply role-based access control (RBAC) principles through Windows PowerShell remote sessions. Instead of allowing users general roles, which often comes hand in hand with to much rights, which aren’t needed to do the daily work, with JEA you can configure special Windows PowerShell endpoints, that provide only the necessary functionality to perform a specific task.
In other words, JEA let’s you lock down a PowerShell session and assigns only the rights needed, this increases the security for your environment.
You configure JEA by creating or editing role-capability files (*.psrc) and session-configuration files (*.pssc).
How to configure
First we create a folder where the module resides. Usually this is in “C:\Program Files\WindowsPowerShell\Modules”
Define the module path
$modulePath = "$env:ProgramFiles\WindowsPowerShell\Modules\JeaSpoolModule"
Create the directory structure
New-Item -ItemType Directory -Path "$modulePath\RoleCapabilities" -ForcCode language: PowerShell (powershell)Now we create a new role-capability file under this path.
New-PSRoleCapabilityFile -Path "$modulePath\RoleCapabilities\Restart-Spooler.psrc"Code language: PowerShell (powershell)The role-capability file handles the “What?” in other words, which commands are allowed to be run.
Now we edit the role-cability file and we add the following to the “VisibleCmdlets”-Section:
VisibleCmdlets = @(
@{
Name = 'Restart-Service'
Parameters = @{
Name = 'Name'
ValidateSet = 'Spooler'
}
}
)Code language: PowerShell (powershell)In the “VisibleCmdlets”-Section you allow certain commands to work, or not work in your PowerShell session, with the “ValidateSet” argument, you tell your PowerShell session exactly for which services this command can be run.
Now we create the session-configuration file similar to the commands above.
# Define the path for the configuration file
$confPath = "$env:ProgramFiles\WindowsPowerShell\Modules\JeaSpoolerModule\SpoolerEndpoint.pssc"
# Generate the file with FullLanguage (we restrict it later via the Role)
New-PSSessionConfigurationFile -Path $confPath -SessionType RestrictedRemoteServer -TranscriptDirectory "C:\Transcripts"Code language: PowerShell (powershell)(Note: I added -TranscriptDirectory because logging is a best practice for JEA, but you can remove it if you don’t have that folder created).
The session-configuration file handles the “Who?” and “How?” like, who gets in and in which room do they go.
In this session-configuration file we map the Users to the Role. In this scenario, I am matching my user to the role “SpoolerRestarter”.
RoleDefinitions = @{
'lenherr\mytestuser' = @{ RoleCapabilities = 'SpoolerRestarter' }
}Code language: PowerShell (powershell)Make sure the name “SpoolerRestarter” matches exactly the filename of your *.psrc created in the previous task.
Check if RunAsVirtualAccount is set to true in the *.pssc
RunAsVirtualAccount = $trueCode language: PowerShell (powershell)Now we register the JEA endpoint:
Register-PSSessionConfiguration -Name "SpoolerMaintenance" -Path "$env:ProgramFiles\WindowsPowerShell\Modules\JeaSpoolerModule\SpoolerEndpoint.pssc" -ForceCode language: PowerShell (powershell)How to test
To test our configuration we enter a PSSession under our testuser and try some cmdlets.
Enter-PSSession -ComputerName localhost -ConfigurationName SpoolerMaintenanceCode language: PowerShell (powershell)Test 1 (should succeed)
Restart-Service SpoolerCode language: PowerShell (powershell)Result:
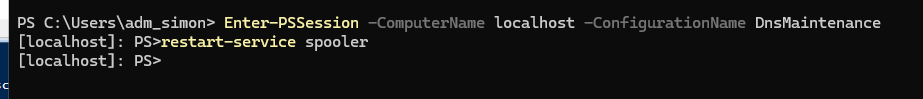
Service gets restarted, works like a charm!
Test 2 (should not be allowed)
Restart-Service WdiServicehostCode language: PowerShell (powershell)Result:
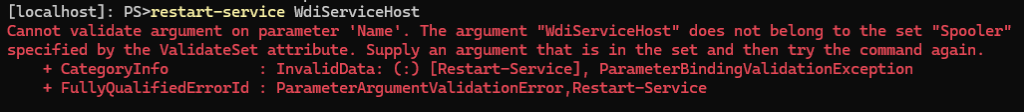
This command is not allowed, so it gives out an error.
We just successfully restricted a PowerShell session to only allow certain cmdlets.